Overview
Smart proxies have become
essential infrastructure components in modern red teaming and penetration testing operations, providing sophisticated anonymization, traffic obfuscation, and operational security capabilities. These advanced proxy solutions enable cybersecurity professionals to conduct thorough security assessments while maintaining stealth, avoiding detection, and ensuring the integrity of their testing methodologies.
Understanding Smart Proxies in Security Testing Context
Smart proxies represent an evolution beyond traditional proxy services, incorporating intelligent routing mechanisms, automated IP rotation, and advanced evasion techniques specifically designed for security testing environments. Unlike standard proxies that simply route traffic through alternative IP addresses, smart proxies leverage sophisticated algorithms to optimize anonymity, bypass detection systems, and maintain operational continuity during complex security assessments.
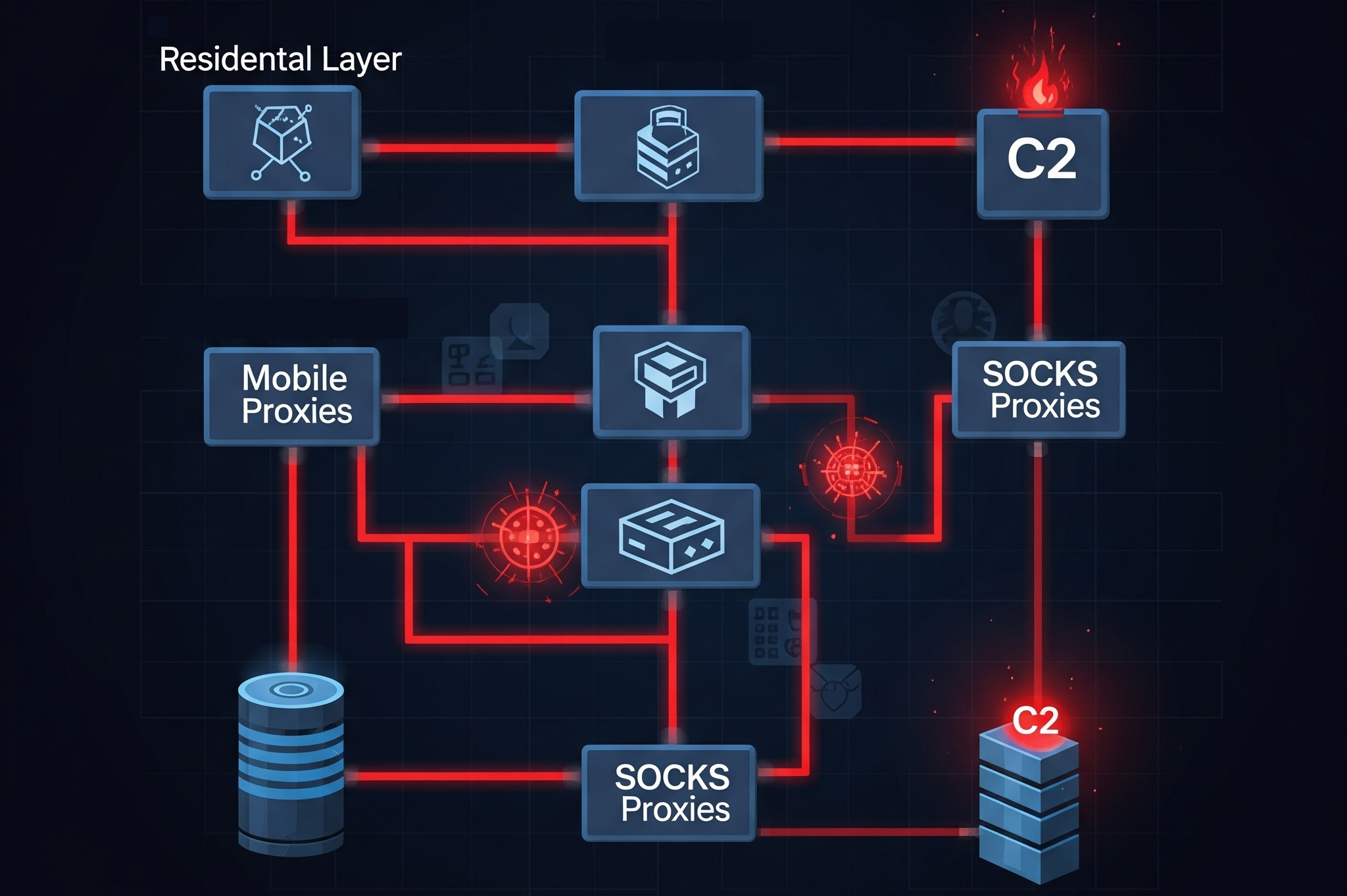
Advanced Proxy Types for Security Testing
Residential Proxies for Enhanced Legitimacy
Residential proxies utilize IP addresses assigned by Internet Service Providers to real households, making them virtually indistinguishable from legitimate user traffic. In red teaming operations, these proxies provide the highest level of authenticity, as they appear as genuine residential users rather than datacenter-based connections that are more easily flagged by security systems.
Mobile Proxies for Dynamic Operations
Mobile proxies route traffic through cellular networks, offering unique advantages for penetration testing scenarios. These proxies are particularly valuable when testing mobile applications or when operations require IP addresses that change frequently due to carrier network dynamics. The natural IP rotation inherent in mobile networks provides additional obfuscation for red team activities.
SOCKS Proxies for Protocol Flexibility
SOCKS proxies provide protocol-agnostic tunneling capabilities, supporting both TCP and UDP traffic. This makes them ideal for comprehensive penetration testing that requires testing various network protocols beyond HTTP/HTTPS. SOCKS5 proxies, in particular, offer enhanced security features including authentication and UDP support, making them valuable for complex network assessments.
Strategic Implementation for Red Team Operations
Infrastructure Design and Deployment
Modern red team operations require sophisticated proxy infrastructure that integrates seamlessly with command and control (C2) frameworks. The infrastructure typically employs multiple layers of proxies, redirectors, and obfuscation mechanisms to protect backend team servers from detection and attribution.
Proxy Chain Configuration
Tools like ProxyChains enable red teams to route traffic through multiple proxy servers in sequence, creating complex anonymization chains that make traffic analysis extremely difficult. The configuration supports dynamic, strict, round-robin, and random chaining modes, each offering different advantages for specific operational requirements.
Dynamic chains provide resilience by automatically bypassing failed proxies, while random chains offer enhanced anonymity by varying the routing path for each connection. This flexibility allows red teams to adapt their proxy usage based on the specific requirements of each engagement.
OPSEC Considerations and Threat Mitigation
Operational Security Through Proxy Diversification
Effective red team operations require careful consideration of operational security (OPSEC) principles when deploying proxy infrastructure. This includes avoiding the reuse of proxy chains across different engagements, implementing geographic diversity in proxy selection, and ensuring that proxy usage patterns do not create identifiable signatures.
Traffic Obfuscation and Evasion
Advanced proxy implementations incorporate traffic obfuscation techniques to defeat network-based detection systems. This includes masking proxy traffic as legitimate application traffic, implementing domain fronting techniques, and using encrypted tunnels that resist deep packet inspection.
Modern adversaries have been observed using multiple layers of anonymization, including commercial VPN services, TOR networks, and residential proxies to mask their operations and complicate attribution efforts. Red teams must employ similar techniques to provide realistic threat simulation.
Technical Integration with Security Testing Tools
C2 Framework Integration
Advanced C2 Proxy Architecture
Modern C2 frameworks like PoshC2 and Mythic provide native proxy awareness and integration capabilities. These frameworks support various proxy types and can automatically route traffic through proxy chains while maintaining encrypted communications with implants.
The integration typically involves configuring proxy redirectors that sit between internet-exposed systems and backend C2 servers. This architecture ensures that C2 infrastructure remains hidden while providing resilient communication channels for red team operations.
Automated Proxy Management
Professional red team operations increasingly rely on automated proxy management systems that handle IP rotation, health monitoring, and failover mechanisms. Tools like ProxyHunter provide centralized management of proxy pools with features like geographic targeting, quality scoring, and performance optimization.
Penetration Testing Tool Integration
Smart proxies enable penetration testers to conduct network reconnaissance from multiple vantage points without revealing their true source IP addresses. This is particularly valuable when testing network segmentation, firewall rules, and intrusion detection systems.
Web Application Testing
For web application penetration testing, smart proxies integrate with tools like Burp Suite, OWASP ZAP, and custom testing frameworks. The proxy integration enables testers to bypass IP-based restrictions and conduct thorough security assessments without triggering rate limiting or blocking mechanisms.
Detection Evasion and Anti-Forensics
Advanced Evasion Techniques
Browser Fingerprinting Resistance
Modern detection systems employ sophisticated fingerprinting techniques to identify automated tools and proxy usage. Smart proxy implementations counter these measures by providing realistic browser fingerprints, randomizing user agent strings, and implementing behavioral patterns that mimic legitimate user activity.
Protocol-Level Evasion
Advanced proxy systems implement protocol-level obfuscation to defeat network-based detection systems. This includes techniques like traffic shaping, protocol tunneling, and encrypted payload delivery that make proxy traffic indistinguishable from legitimate application traffic.
Probe Resistance and Resilience
Active Probing Countermeasures
Security-focused proxy implementations include probe resistance mechanisms that prevent network defenders from identifying proxy servers through active scanning techniques. These systems remain silent when probed by unauthorized entities and only respond to authenticated requests.
Geographic and Temporal Dispersion
Effective evasion requires geographic and temporal distribution of proxy usage. This involves selecting proxies from different regions, implementing realistic timing patterns, and avoiding behaviors that create detectable signatures in network traffic analysis.
Legal and Ethical Considerations
Authorized Testing Boundaries
Engagement Scope and Authorization
Red team operations must operate within clearly defined legal boundaries established by client agreements and engagement letters. This includes ensuring that proxy usage is explicitly authorized and that all activities remain within the scope of the authorized testing.
Third-Party Service Compliance
When utilizing commercial proxy services, red teams must carefully review terms of service and ensure compliance with provider policies. Some proxy services explicitly prohibit security testing activities, while others may require prior notification or special authorization.
Risk Mitigation Strategies
Documentation and Accountability
Proper documentation of proxy usage, including detailed logs of all activities and clear justification for security testing actions, is essential for legal protection. This documentation should demonstrate that all activities were conducted within authorized boundaries and for legitimate security testing purposes.
Professional Liability Considerations
Organizations conducting red team operations should ensure appropriate professional liability coverage that includes activities involving proxy usage and security testing. This protection becomes particularly important when testing involves third-party services or cloud-based infrastructure.
Advanced Operational Techniques
Multi-Stage Proxy Architectures
Layered Anonymization Systems
Professional red team operations employ multi-stage proxy architectures that combine different proxy types and technologies. This might include routing traffic through residential proxies, then through SOCKS tunnels, and finally through domain fronting services to create multiple layers of obfuscation.
Automated Failover and Redundancy
Enterprise-grade proxy systems implement automated failover mechanisms that ensure operational continuity even when individual proxy nodes are discovered or blocked. This includes maintaining multiple proxy pools, implementing health monitoring, and providing automatic failover to backup infrastructure.
Performance Optimization
Load Balancing and Distribution
Smart proxy implementations include intelligent load balancing that distributes traffic across multiple proxy nodes to optimize performance and avoid overwhelming individual proxies. This is particularly important for large-scale security assessments that generate significant network traffic.
Quality Scoring and Selection
Advanced proxy management systems implement quality scoring algorithms that automatically select the most appropriate proxies based on factors like latency, reliability, geographic location, and detection risk. This ensures optimal performance while maintaining security objectives.
Conclusion
Smart proxies are essential for red teaming and penetration testing, offering anonymization and evasion needed for effective security assessments. Integrated with C2 frameworks, automation, and evasion techniques, they help security pros test while maintaining OPSEC. The evolution of proxies—like residential, mobile, and intelligent routing—enhances detection bypassing and realistic threat simulations. Their success depends on proper use, OPSEC, and legal compliance. As defensive technologies improve, red team proxies must evolve with new evasion techniques and automated management. The future of red team proxy operations lies in adaptive systems that stay ahead of threats while ensuring anonymity and security. Organizations investing in these technologies will provide better, more accurate security assessments.
